MIT CoLab on X: "Saturday: Join Boston neighbors, activists, archivists, and students who are #HackingTheArchive. We're hacking the racial wealth gap by exploring the strategies of past activists' whose actions can guide

Did #GAP's Instagram get hacked? It's now posting #YZY designs after deleting all of its previous photos and making the YZY brand logo its… | Instagram

Gap seeking over $2M from Kanye West to cover potential damages incurred in lawsuit accusing retail giant of breach of contract

Hacking the Gap: A Journey from Intuition to Innovation and Beyond - Kindle edition by Voisen, Greg. Self-Help Kindle eBooks @ Amazon.com.

Hacking Leadership: The 11 Gaps Every Business Needs to Close and the Secrets to Closing Them Quickly | Wiley
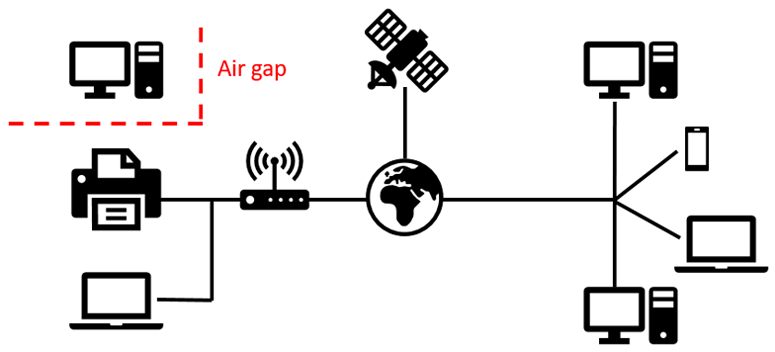
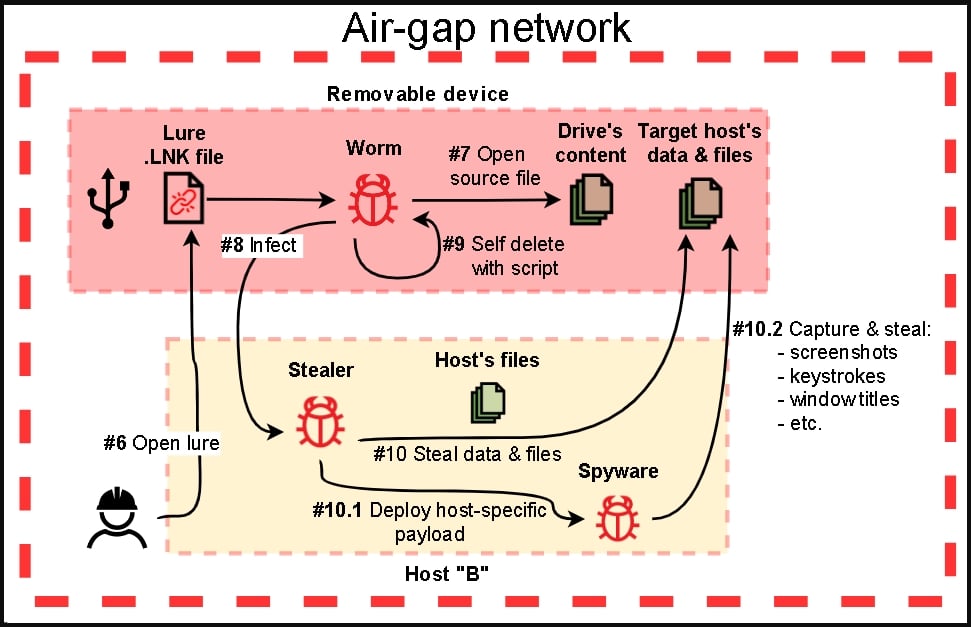
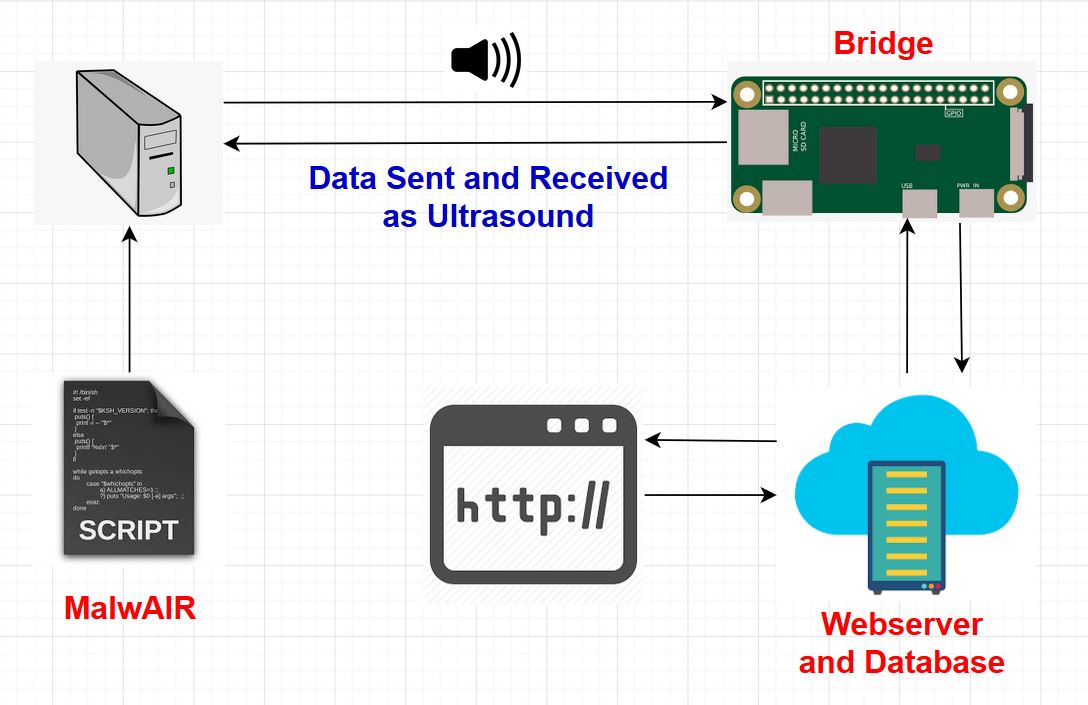
Hacking the Air Gap: Stealing Data from a Computer that isn't Connected to the Internet | Science Project